Ans: Yes! They are still used even today in the management of large-scale remote access. This networking device is especially famous in corporate environments that manage hundreds or thousands of remote or hybrid workers securely.
What Is A VPN Concentrator? Purpose, Types, Usage & More
VPN concentrators soared to prominence in the IT circle due to their significant role in enhancing the capabilities of millions of work-from-home employees. Understanding what is a VPN concentrator is the first step to know how remote connections are handled in corporate environments.
If you are planning to integrate them in your corporate setting, you should know in detail what it is, its types, and its purpose.
- What is a VPN Concentrator?
- How does a VPN Concentrator work?
- What is the Purpose of a VPN Concentrator?
- What are the Different Types of VPN Concentrators?
- How to Use a VPN Concentrator?
- What Alternatives of VPN Concentrators Can I Use?
- Top 4 VPN Concentrators Available in the Market
- VPN Concentrator Pros and Cons
- VPN vs. VPN Concentrator
- VPN Gateway vs. Concentrator
- Bottomline
- FAQs
What is a VPN Concentrator?
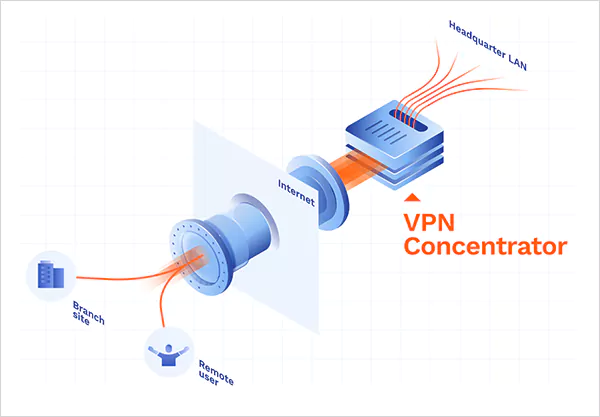
A VPN concentrator is a networking device that creates and manages multiple VPN tunnels simultaneously. It is especially used for remote access in large enterprises managing thousands of remote workers at the same time. In the era of hybrid work and sophisticated cyber threats, the VPN concentrator is a hidden gem in corporate cybersecurity.
How Does a VPN Concentrator Work?
A VPN concentrator is typically placed behind a firewall to provide secure access to geographically dispersed employees. It creates an individual encrypted tunnel (using protocols like SSL and IPsec) between each worker and the corporate network, keeping data inaccessible to any unauthorized party.
Through this, VPN concentrators handle all the work, from managing connections and authenticating users to routing traffic securely from the mobile remote employees and the internal network resources.
You may also read: Best VPN for USA in 2025: Top Picks for Privacy, Streaming & Speed
What is the Purpose of a VPN Concentrator?
What is a VPN concentrator used for? Its purpose is to handle hundreds and thousands of secure, encrypted tunnels, allowing branch offices and remote workers secure access. It is the best solution for enterprise-level settings like government offices, healthcare systems, and educational institutions that are managing multiple remote access VPN connections.
- Centralized Connection Management: A VPN concentrator is designed to serve as a central point for handling multiple devices for remote access and site-to-site connections.
- Encrypted Tunneling: This ensures that employees’ traffic is encrypted using protocols like SSL and IPsec, keeping data inaccessible to unauthorized parties.
- Authentication and Access Control: It authenticates users by verifying credentials and assigns a unique IP address to identify them within the network.
- Performance Optimization: It improves network performance by doing all resource-intensive processes of encryption and decryption and offloading the main firewall.
- Data Traffic Routing: It encrypts the outgoing data from the network to the remote user and, conversely, decrypts the data from the remote user to the network.
What are the Different Types of VPN Concentrators?
A VPN concentrator is a networking device that is designed to encrypt connections between two distinct points. According to the points, they are classified into many types, including remote access concentrator, site-to-site concentrator, and mobile concentrator. Let’s understand what is a VPN concentrator type that works best for you:
1. Remote Access VPN Concentrator
This type is designed keeping in mind the employees who are working remotely to connect them to a private, secure network over the internet.
2. Site-to-Site VPN Concentrator
A site-to-site VPN concentrator typically operates with IPsec encryption. It connects entire networks, for instance, branch offices and head offices.
3. SSL VPN Concentrator
This networking product is a highly flexible one. It uses SSL/TLS protocols, offering clientless access, typically through a web browser.
4. Cloud VPN Concentrator
It connects remote users or site-to-site networks to a cloud infrastructure. It is virtualized and directly integrated into the cloud network, unlike traditional hardware types.
5. Mobile VPN Concentrator
Mobile VPN Concentrator is specialized for mobile users, keeping sessions active when the individual is switching between cellular networks and Wi-Fi. It connects thousands of VPN tunnels of mobile or telecommuting employees to a central network.
How to Use a VPN Concentrator?
Most of us found it difficult to install and use, mostly requiring expert guidance. However, we can simplify the process of their use by arranging it in easy-to-understand steps. They work differently for a user and administrator from the initial installation to the end setup.
User Perspective
- Install: Install the VPN client that is provided by your organization.
- Authenticate: Launch the app and enter your username and password (often a multi-factor authentication code is also required).
- Connect: Click “connect,” and you will get an encrypted tunnel. The concentrator will also provide you with an IP address and start managing secure traffic.
- Access Resources: Now connected, you can access company resources, including files and servers, as you do by being physically present in the office.
Administrator’s Perspective
- Install: Place the virtual or physical concentrator at the edge of the corporate networks.
- Configure: Next, configure the network settings, for instance, IP address, protocols (SSL or IPsec), and routing rules through the device management console.
- Define Access Policies: Set up policies to designate which users can access which company resources.
- Setup: Now configure site-to-site VPN tunnels if you have branch offices. It often requires BGP routing and pre-shared keys or certification.
What Alternatives of VPN Concentrators Can I Use?
Though, they focus on modernizing the current hybrid workforce, there are some flexible and equally secure options available to us, including Zero Trust Network Access (ZTNA), Secure Access Service Edge (SASE), and Software-Defined Perimeter (SDP), if you don’t find a VPN concentrator suited for you.
- Zero Trust Network Access (ZTNA): This is an ideal replacement for a VPN concentrator. It grants access to each application rather than a whole network, offering enhanced security.
- Secure Access Service Edge (SASE): SASE is a preferred alternative for a VPN concentrator, as it combines networking (SD-WAN) and security (ZTNA, SWG, CASB) into a single platform.
- Software-Defined Perimeter (SDP): SDP makes an invisible software boundary around the company’s resources rather than a physical one. It helps hide them from public access before the authentication is verified.
Top 4 VPN Concentrators Available in the Market
What is a VPN concentrator that is becoming customers’ top choice? There are many affordable and high-quality options available to you if you are planning to buy it including Cisco Meraki (MX Series) and Fortinet FortiGate (6000F/6500F Series). They are designed to work effectively in medium to large enterprise environments:
1. Fortinet FortiGate (6000F/6500F Series)
Fortinet FortiGate is rated as the top choice for large-scale secure networking because of its great price-to-performance through custom silicon. With up to 9 Gbps IPsec throughput, the device can handle high traffic.
2. Cisco Meraki (MX Series)
Cisco Meraki provides “AutoVPN,” which leads to easy setup for branch offices and remote employees. It is ideal for dispersed enterprises because of its cloud-managed networks.
3. Mako Networks (7000/8000 Series)
Mako Networks works on cloud-based management and can handle thousands of VPN tunnels at the same time. The PCI-certified devices are specifically designed for distributed and retail enterprises.
4. Juniper Networks (SRX5400)
Juniper Networks is the best choice for massive deployment or large-scale enterprises. The devices can handle millions of sessions and support up to 188 Gbps of throughput.
VPN Concentrator Pros and Cons
There are many pros of installing a VPN concentrator, as it ensures network stability and handles thousands of VPN tunnels at the same time. However, its use is not suitable for every enterprise. Its cons can involve a complex setup and high initial cost. Let’s see in detail:
| Pros | Cons |
| Ensures network stability and handles a high number of connections at the same time for remote employees. | They require a high initial cost, which is the reason they are well-suited for large-scale enterprises. |
| Provides centralized access control and security management from a single central point. | If the concentrator fails, all the connected remote access gets disrupted. |
| Protects against data breaches by advanced encryption and authentication. | Maintenance and troubleshooting require dedicated IT expertise. |
| Quicker method to generate hundreds and thousands of VPN tunnels than individual VPNs. |
VPN vs. VPN Concentrator
Many people tend to confuse a VPN with a VPN concentrator, but in reality, they work very differently on the basis of scalability, purpose, use, and performance.
| Features | VPN | VPN Concentrator |
| Scalability | Connects one user. | Can connect hundreds and thousands of users. |
| Implementation | It is a technology, a software, or a protocol. | It is a specialized hardware application or a virtual appliance. |
| Performance | Offers comparatively low performance. | Handle heavy encryption loads and offer high performance. |
| Purpose | To provide secure and reliable access. | To handle multiple remote users simultaneously and securely. |
| Usage | Remote workers, a small business, or an individual want secure data. | Medium to large-scale enterprises with a high number of employees. |
VPN Gateway vs. Concentrator
What is a VPN concentrator, and what is the VPN gateway difference? Most of the people use these terms interchangeably in their daily lives. So it is necessary to differentiate them based on features like capacity and centralization for a better understanding.
| Features | VPN Concentrator | VPN Gateway |
| Capacity | Medium to large-scale enterprises | Can be useful for smaller settings like home VPN routers and cloud-based systems. |
| Device | A specialized device that manages multiple VPN tunnels. | It can be anything: a router, a server, a firewall, or another dedicated device that can connect the local network to the VPN network. |
| Software vs. Hardware | Piece of on-site hardware | Virtualized and software-defined |
| Centralization | Acts as a central hub for security enforcement and management. | Provides a more versatile option in both smaller settings and dispersed environments but may lack in high-performance throughput. |
| Best For | Medium to large-scale enterprises that have a large number of hybrid or remote workers. | Small branch offices that are working on cloud-based or software defined networks. |
Bottom Line
VPN concentrators have become unsung heroes of many medium to large enterprises in the advent of the hybrid work mode. While it’s going overboard to use it in small businesses and for personal usage, these devices remain very significant in handling thousands of workers at the same time securely in the era of evolving cyber threats. Hope, now you know what is a Vpn Concentrator.
FAQs
Q: Are VPN concentrators still used?
Q: Is a VPN concentrator a physical device?
Ans: Yes! It is a physical hardware device that is designed to manage secure and large-scale VPN tunnels.
Q: Do I need a VPN concentrator?
Ans: Yes, if you have a medium- to large-scale enterprise and have to manage hundreds to thousands of remote employees. However, if you own a small enterprise, it’s not needed in that case.
Q: Where should a VPN concentrator be installed?
Ans: Install it in the network parameter, best when placed behind the firewall or in your DMZ (demilitarized zone). This position allows for authenticating and encrypting traffic before it enters the internal network.
Sources: